Configuring Microsoft Entra ID user settings
2026-01-30Last updated
To define how identity data flows between Microsoft Entra ID and Genetec ClearID™, you must configure your user settings and map attributes for automatic synchronization.
Before you begin
What you should know
Procedure
- In the Microsoft Azure portal, search for and click Enterprise applications.
- In the Enterprise applications section, search for and select your ClearID SCIM integration application.
- In the Manage section, click Provisioning and then click Provisioning again.
- Expand the Mappings section and click Provision Microsoft Entra ID Users.
-
Modify the default attribute
mappings.
-
On the Attribute Mapping page, click
Delete to remove unused default attributes.
Only keep the following:
userNameactivedisplayName
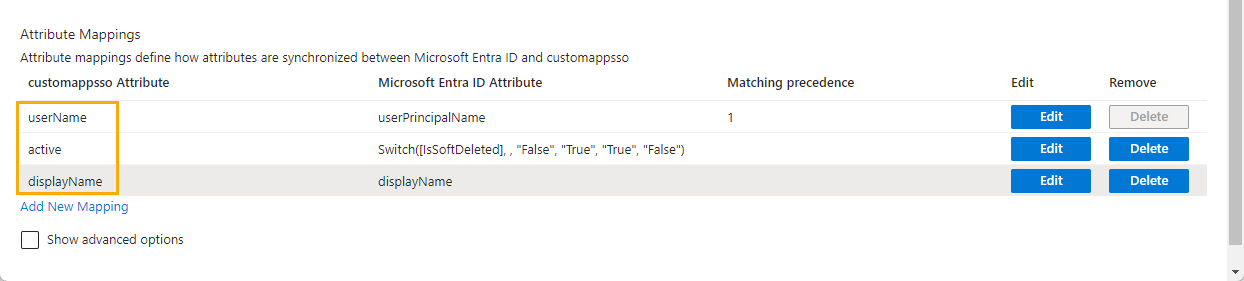
- Click Save and then click Yes to confirm your changes.
-
On the Attribute Mapping page, click
Delete to remove unused default attributes.
-
Modify the customappsso user attributes.
- On the Attribute Mapping page, click Show advanced options.
-
Click Edit attribute list for customappsso, and then click
Delete to remove all the unused default attributes.
Only keep the following:
idactivedisplayNametitleuserName
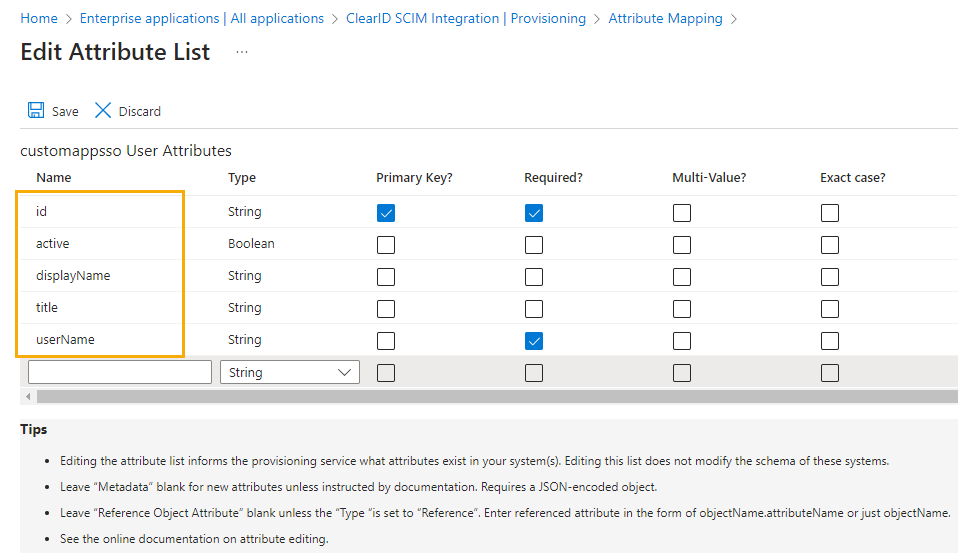
- Click Save and then click Yes to confirm your changes.
-
Add the ClearID schema attributes.
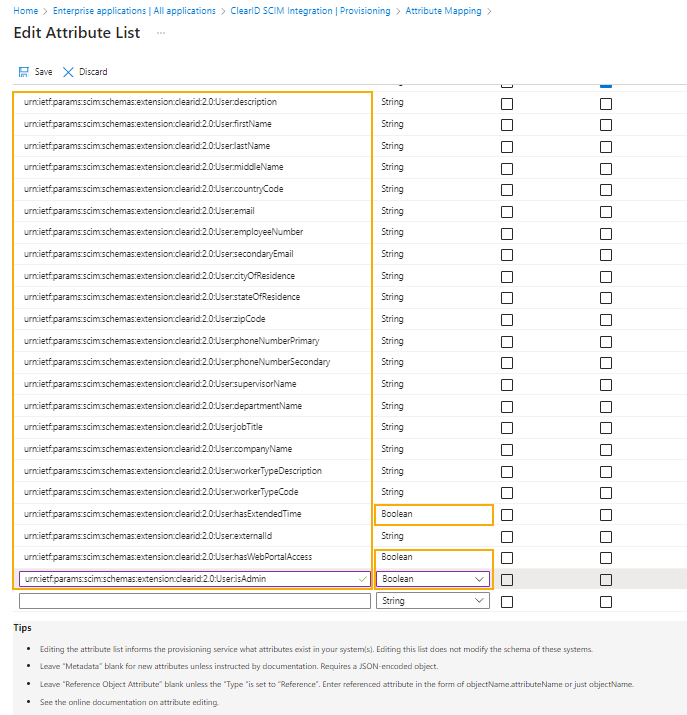
Only include the list of attributes available to ClearID:
urn:ietf:params:scim:schemas:extension:clearid:2.0:User:description urn:ietf:params:scim:schemas:extension:clearid:2.0:User:firstName urn:ietf:params:scim:schemas:extension:clearid:2.0:User:lastName urn:ietf:params:scim:schemas:extension:clearid:2.0:User:middleName urn:ietf:params:scim:schemas:extension:clearid:2.0:User:countryCode urn:ietf:params:scim:schemas:extension:clearid:2.0:User:email urn:ietf:params:scim:schemas:extension:clearid:2.0:User:employeeNumber urn:ietf:params:scim:schemas:extension:clearid:2.0:User:secondaryEmail urn:ietf:params:scim:schemas:extension:clearid:2.0:User:cityOfResidence urn:ietf:params:scim:schemas:extension:clearid:2.0:User:stateOfResidence urn:ietf:params:scim:schemas:extension:clearid:2.0:User:zipCode urn:ietf:params:scim:schemas:extension:clearid:2.0:User:phoneNumberPrimary urn:ietf:params:scim:schemas:extension:clearid:2.0:User:phoneNumberSecondary urn:ietf:params:scim:schemas:extension:clearid:2.0:User:supervisorName urn:ietf:params:scim:schemas:extension:clearid:2.0:User:departmentName urn:ietf:params:scim:schemas:extension:clearid:2.0:User:jobTitle urn:ietf:params:scim:schemas:extension:clearid:2.0:User:companyName urn:ietf:params:scim:schemas:extension:clearid:2.0:User:workerTypeDescription urn:ietf:params:scim:schemas:extension:clearid:2.0:User:workerTypeCode urn:ietf:params:scim:schemas:extension:clearid:2.0:User:hasExtendedTime urn:ietf:params:scim:schemas:extension:clearid:2.0:User:externalId urn:ietf:params:scim:schemas:extension:clearid:2.0:User:hasWebPortalAccess, Boolean urn:ietf:params:scim:schemas:extension:clearid:2.0:User:isAdmin, Boolean-
On the Edit Attribute List page, copy and paste an attribute
name from the preceding ClearID schema attributes code example into the
Name field and select the attribute
Type.
Almost every attribute has the type String, except for three attributes that have the Boolean type:
hasExtendedTime,hasWebPortalAccess, andUserisAdmin.Important:The ClearIDexternalIdattribute is the unique identifier that ClearID uses for synchronization. It’s mapped to the uniqueobjectIdattribute in Microsoft Entra ID. -
Repeat for each attribute listed in the preceding ClearID schema attributes code
example.
- Click Save and then click Yes to confirm your changes.
-
On the Edit Attribute List page, copy and paste an attribute
name from the preceding ClearID schema attributes code example into the
Name field and select the attribute
Type.
-
Add the ClearID attribute mappings.
- On the Attribute Mapping page, click Add New Mapping.
-
On the Edit Attribute page, add the attributes that you
require from the attributes added earlier in step 7.
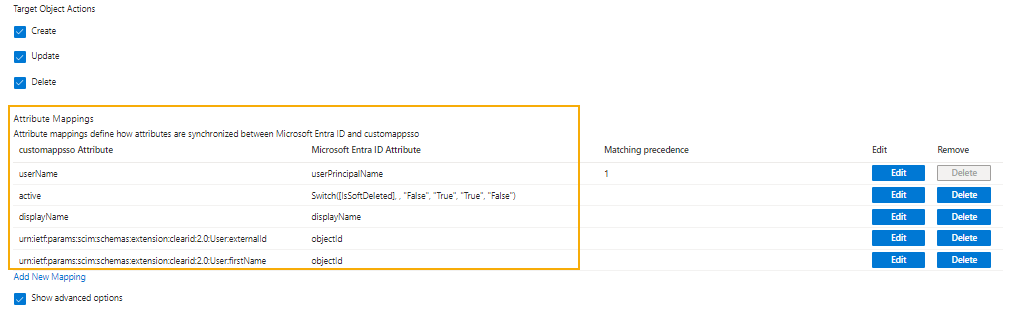
Include the following:
- Mapping type: Direct
- Source attribute: objectid
- Target attribute: <your attribute value>
- Click OK.
-
Repeat for each attribute added earlier and replace the target attribute value with
the next attribute you want to
add.
For a successful first synchronization, you need the following attributes. You can add more attributes later.
 Note:The
Note:Theobjectidis the GUID in azure. It’s a hard-coded, system-generated value that can’t be changed. -
Click Save and then click Yes to
confirm your changes.
You can now close the window and return to the Provisioning page.
