About Microsoft Entra ID synchronization
Microsoft Entra ID is a multi-tenant cloud-based directory and identity management service that combines core directory services, application access management, and identity protection. The Azure web app is used to connect Genetec ClearID™ to Microsoft Entra ID so that user information can be accessed and synchronized.
Connection information for Microsoft Entra ID
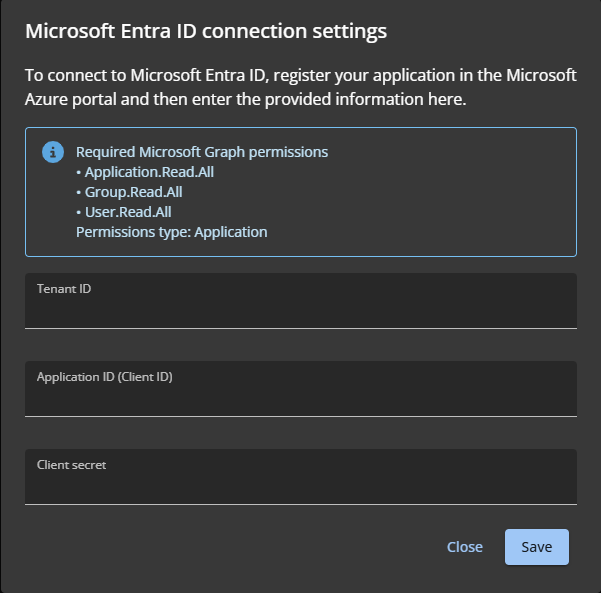
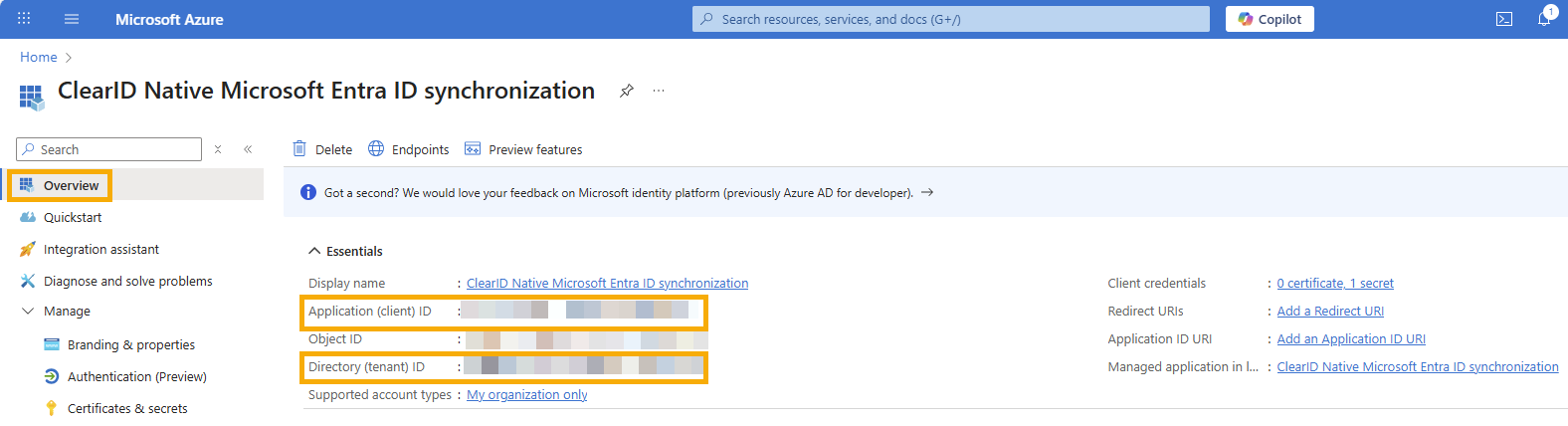
- Tenant ID
- Application ID (Client ID)
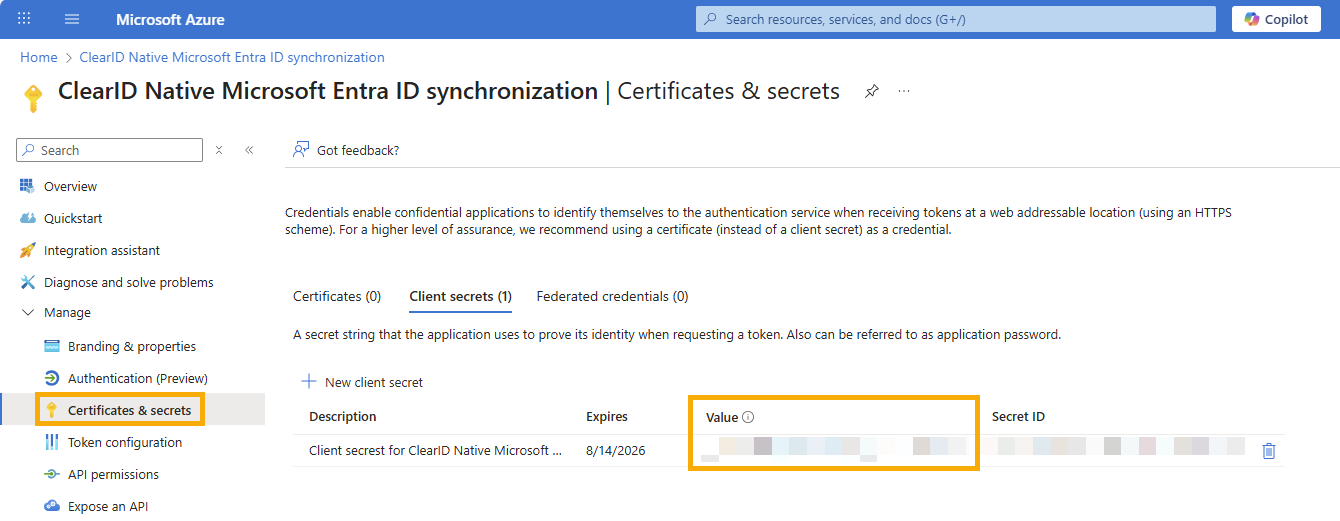
- Client secret
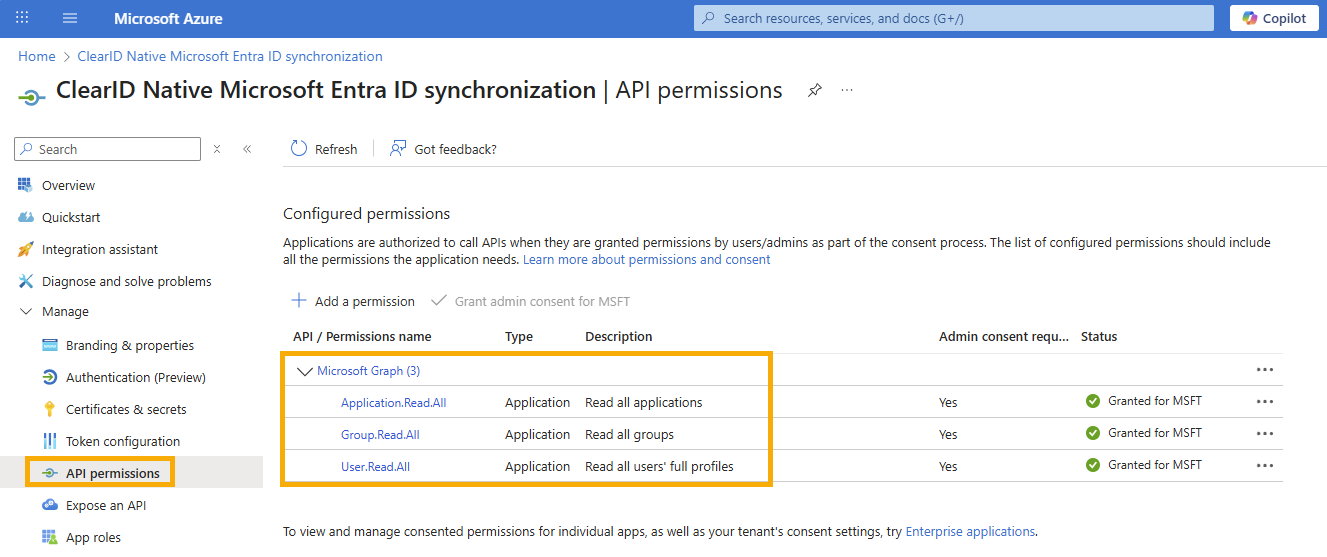
Microsoft Entra ID API permissions
Before you can synchronize data with ClearID, an external system attributes administrator (IT or security personnel) must set up and configure the following API read permission privileges in Microsoft Entra ID. Only Application-type permissions are compatible with the native Microsoft Entra ID synchronization in ClearID.
- Application.Read.All - Used to get extension attributes.
- Allows the app to read applications and service principals without a signed-in user.
For more information, see List extensionProperties (directory extensions)
- User.Read.All - Used to get user information.
- Allows the app to read identity user risk information for all users in your organization without a signed-in user.
- Group.Read.All - Used to get group information.
- Allows the app to read group properties and memberships, and read conversations for all groups, without a signed-in user.
For more information, see Microsoft Graph permissions reference.
